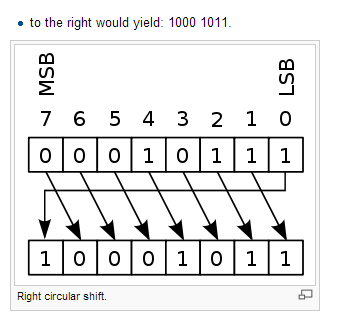
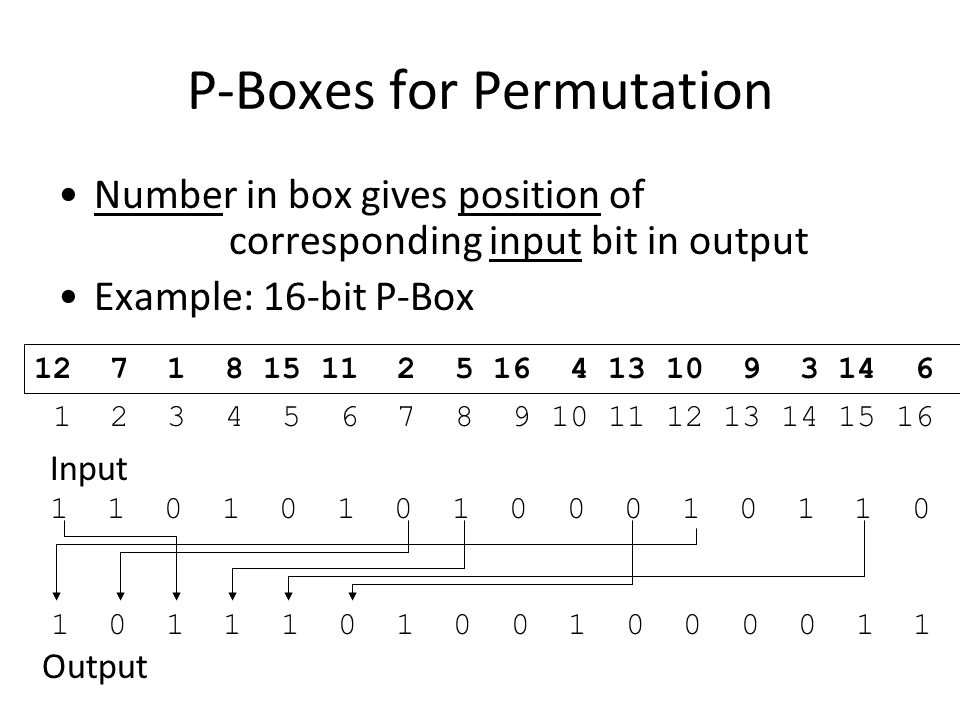
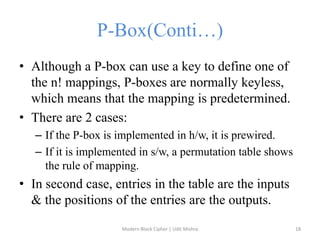
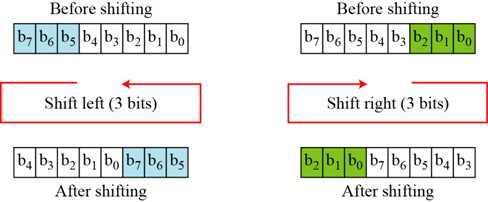
![9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book] 9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book]](https://www.oreilly.com/api/v2/epubs/9780471947837/files/images/ch009-t006.jpg)
9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book]
INTRODUCING DYNAMIC P-BOX AND S-BOX BASED ON MODULAR CALCULATION AND KEY ENCRYPTION FOR ADDING TO CURRENT CRYPTOGRAPHIC SYSTEMS

P-box and S-box: (a) ordinary P-box; (b) compressed P-box; (c) expanded... | Download Scientific Diagram

feistel network - What is the security gain of applying Two S-boxes in Different Ways? - Cryptography Stack Exchange

P-box and S-box: (a) ordinary P-box; (b) compressed P-box; (c) expanded... | Download Scientific Diagram
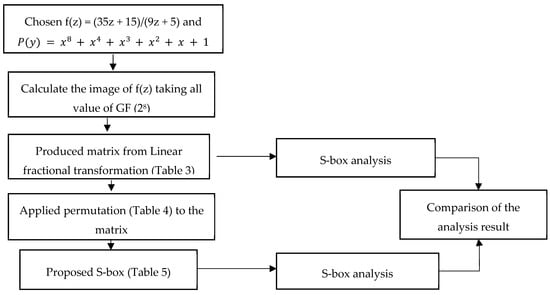
Symmetry | Free Full-Text | S-box Construction Based on Linear Fractional Transformation and Permutation Function

A new image encryption scheme with Feistel like structure using chaotic S- box and Rubik cube based P-box | SpringerLink

P-box and S-box: (a) ordinary P-box; (b) compressed P-box; (c) expanded... | Download Scientific Diagram

Function S-box S1 (in the DES algorithm) represented as a table and its... | Download Scientific Diagram